Configuring Key Management Service (KMS) for Secure Data Encryption
This document provides instructions for creating a Customer Managed Key (CMK) in AWS Key Management Service (KMS). The CMK is used to encrypt and decrypt sensitive data securely. After creating the key, you will need to share its Amazon Resource Name (ARN) with the Unravel team, so they can use it for encryption and decryption operations. Following these steps will result in a fully managed KMS key with the appropriate permissions for Unravel operations, ensuring secure handling of your data.
AWS KMS Key Creation
Using the AWS Console
To gain more control over the key, create a Customer Managed Key (CMK) using the AWS Management Console:
Log in to the AWS Management Console.
Navigate to AWS KMS by searching for KMS in the service search bar.
In the KMS dashboard, select Customer-managed keys in the left navigation pane.
Click Create key.
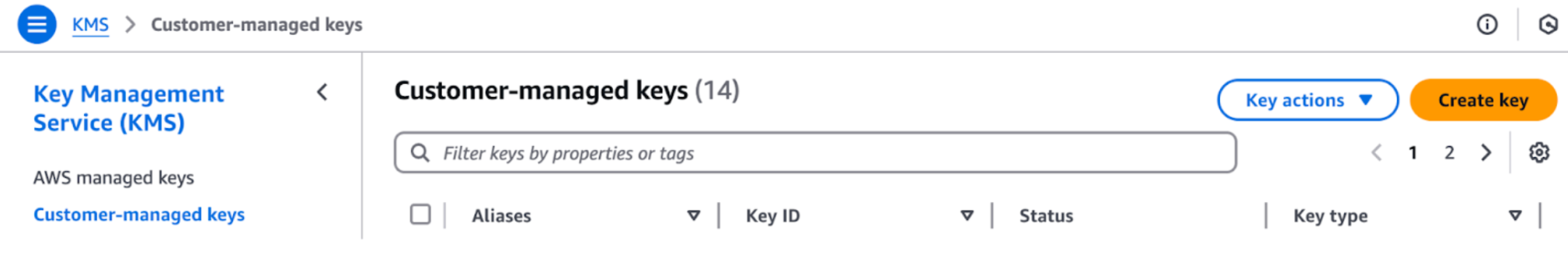
Choose Symmetric Key (recommended for most use cases).
Select Encrypt and decrypt as the key usage.
Configure key details:
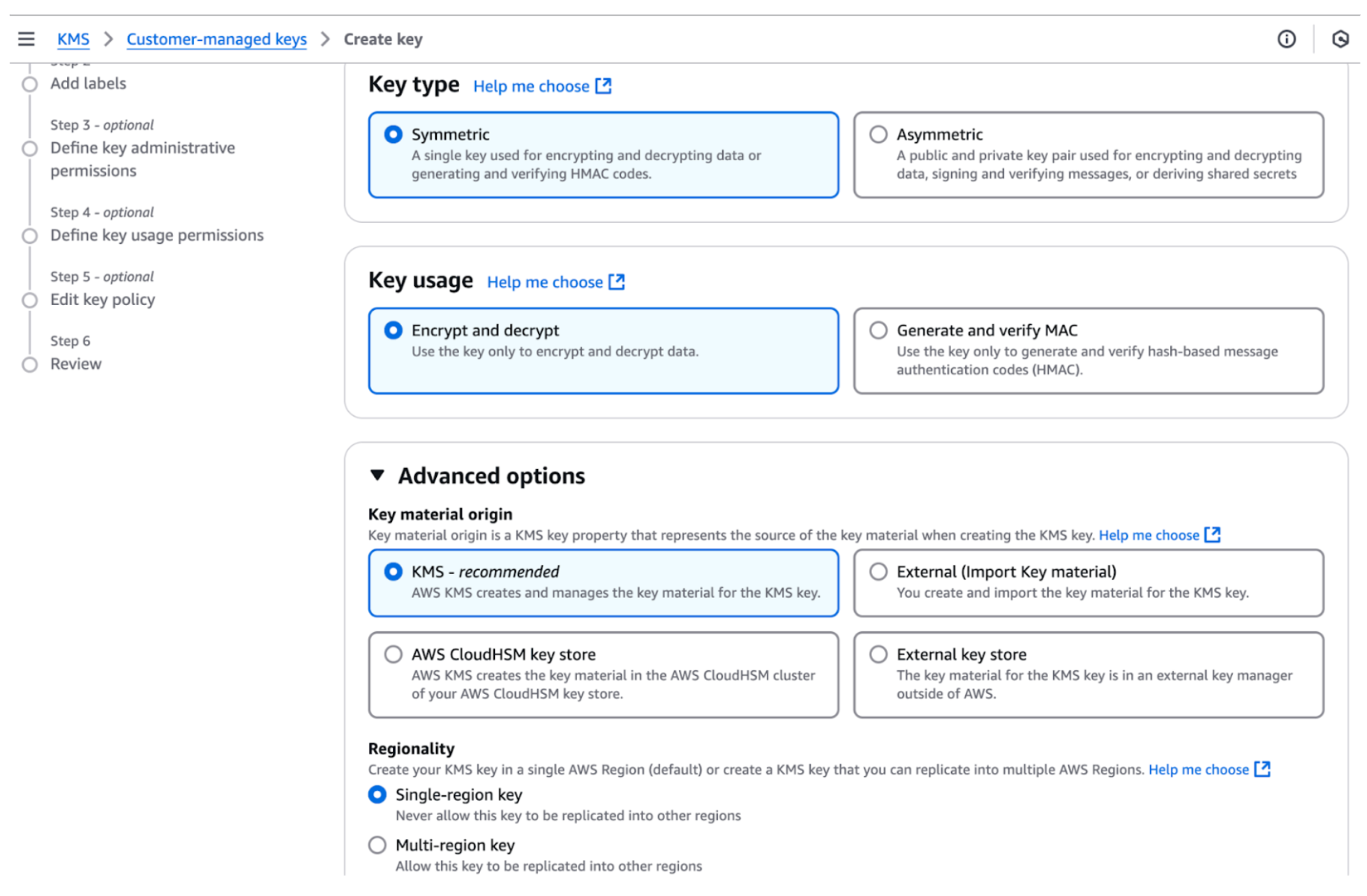
Key name: Enter a recognizable name.
Key description: Optionally, add a description.
Key material origin: AWS KMS.
Regionality: Single-region key.
Add labels. Assign an alias name for easier identification.
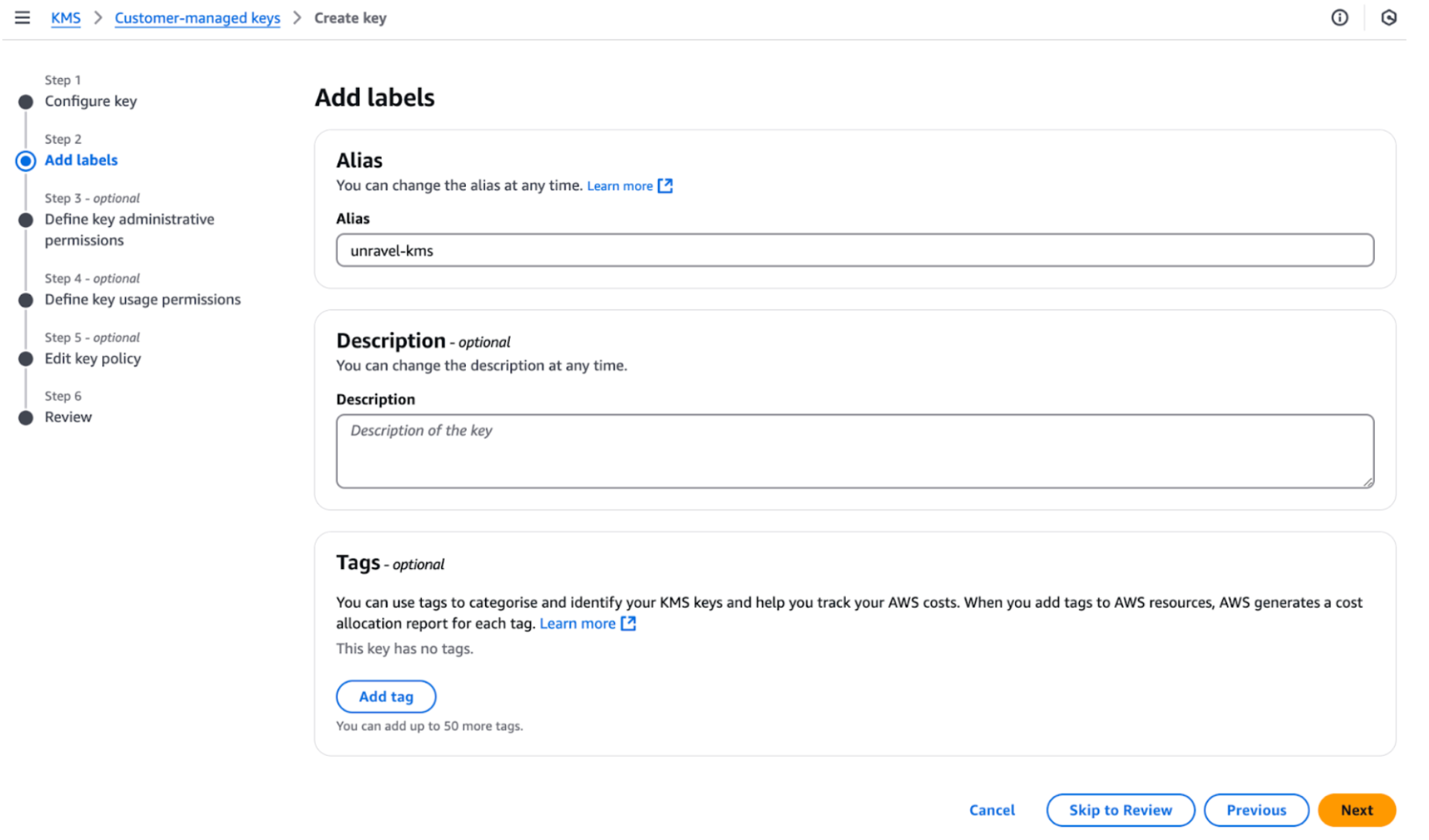
Assign key administrators. Add an IAM user to manage the KMS key.
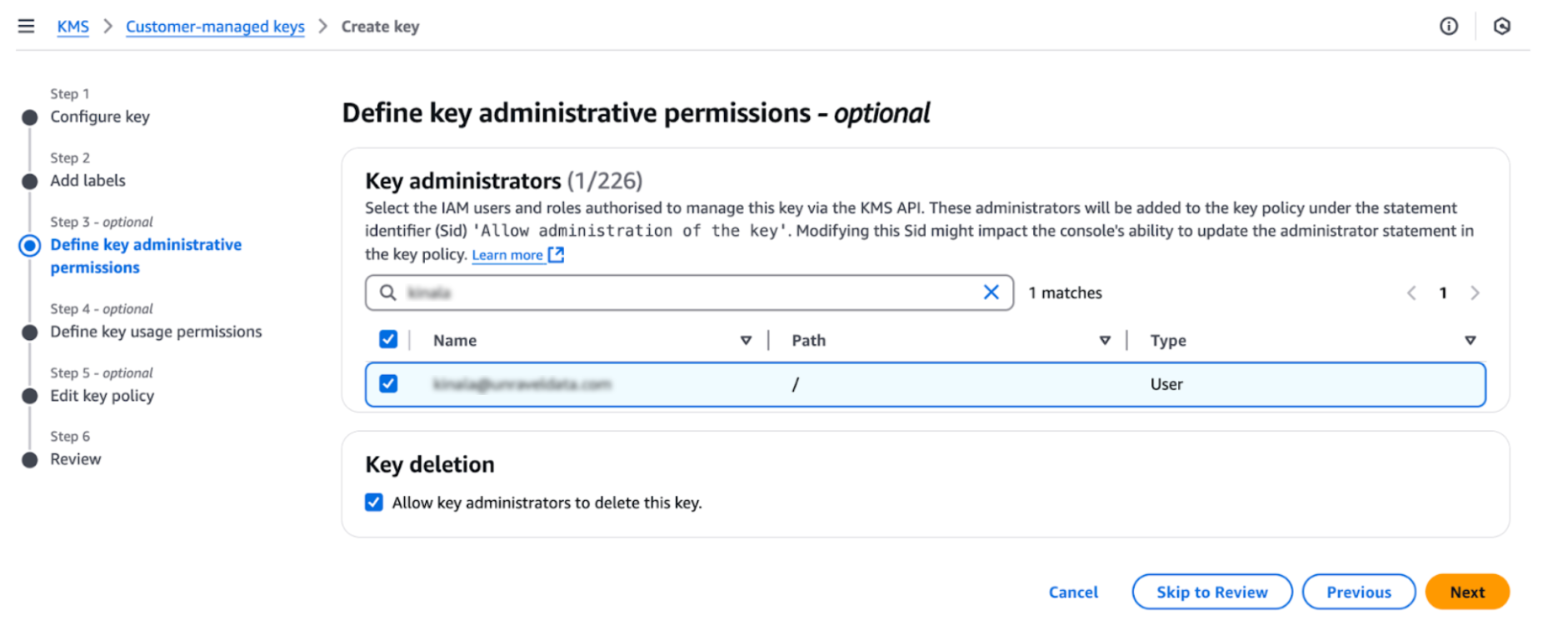
Add Unravel AWS account for access. Unravel Account ID: 848625246342.
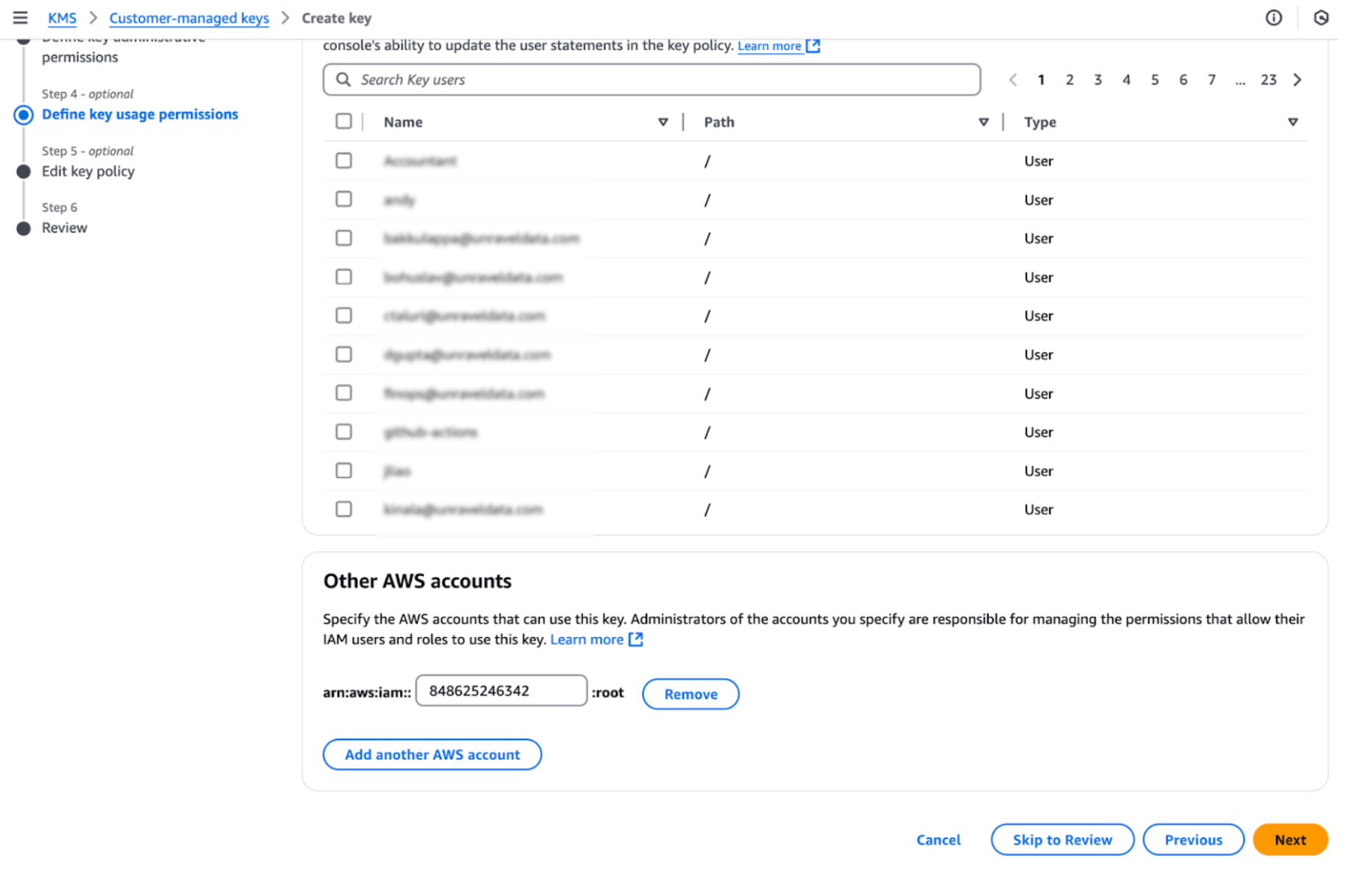
Review the configuration and click Create key.
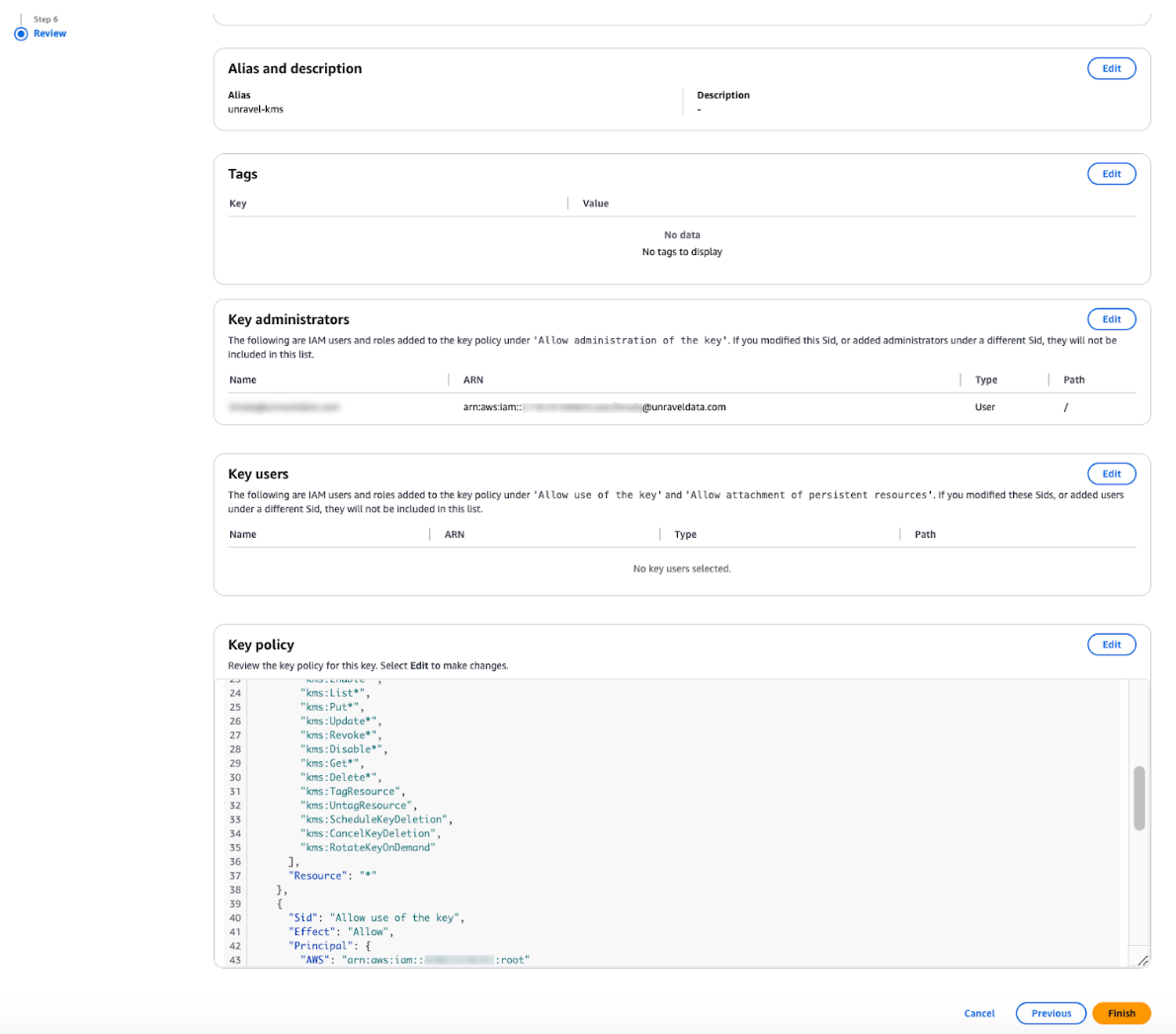
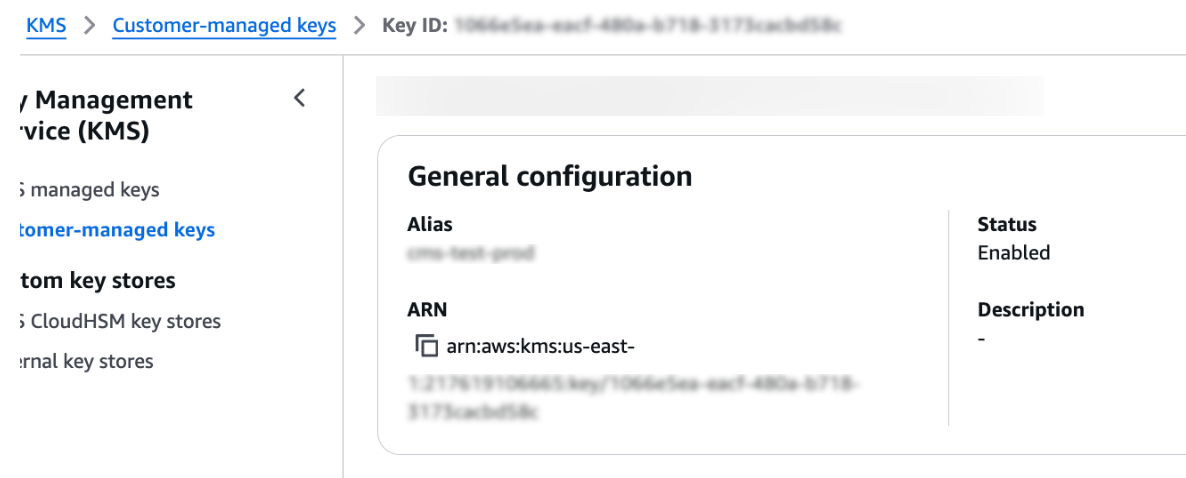
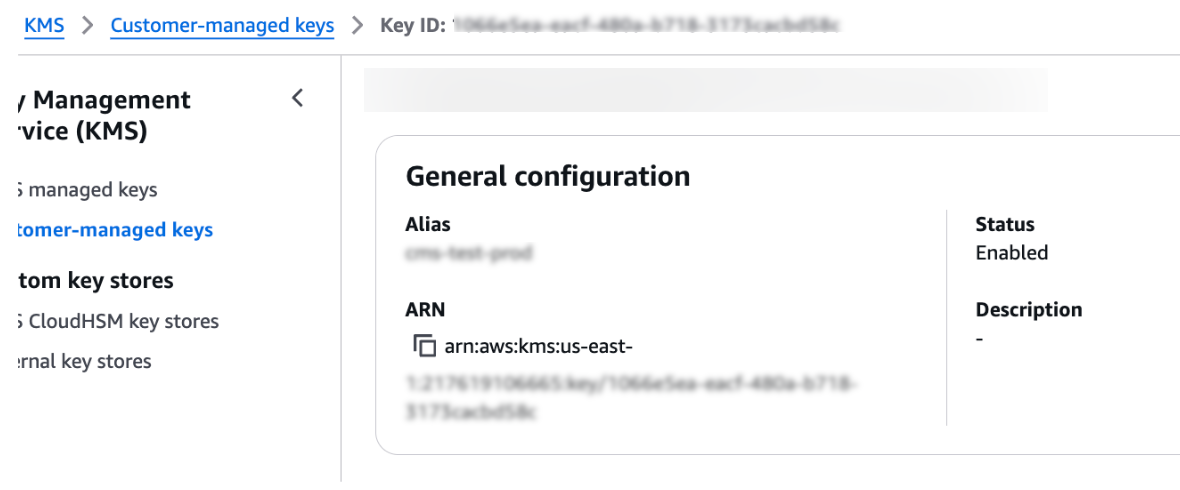
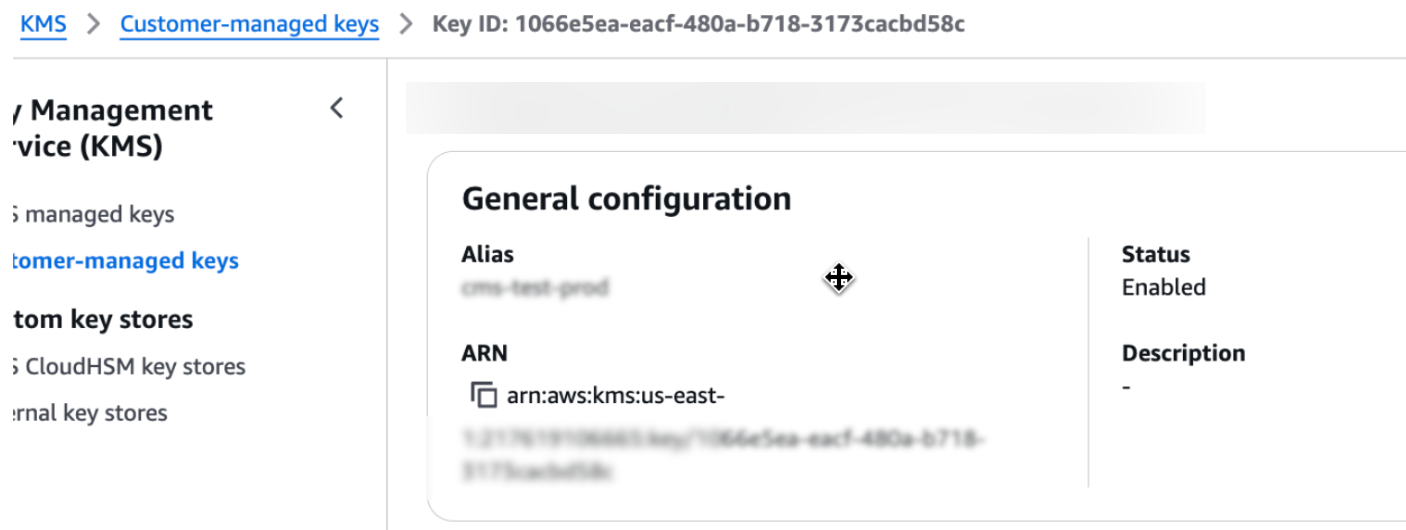
After creating the key, share the AWS ARN with the Unravel team. You can find this in the key description.
Using the AWS CLI
To create a Customer-Managed Key (CMK) using the AWS CLI:
Create the Policy Document.
Save the following JSON policy as policy.json. Replace placeholders with your values:
${CURRENT_AWS_ACCOUNT_ID}: Your AWS account ID where the KMS key is being created.
${ADMIN_USER_ARN}: ARN of the IAM user or role that will manage the KMS key.
{ "Id": "key-consolepolicy-3", "Version": "2012-10-17", "Statement": [ { "Sid": "Enable IAM User Permissions", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::${CURRENT_AWS_ACCOUNT_ID}:root" }, "Action": "kms:*", "Resource": "*" }, { "Sid": "Allow access for Key Administrators", "Effect": "Allow", "Principal": { "AWS": "${ADMIN_USER_ARN}" }, "Action": [ "kms:Create*", "kms:Describe*", "kms:Enable*", "kms:List*", "kms:Put*", "kms:Update*", "kms:Revoke*", "kms:Disable*", "kms:Get*", "kms:Delete*", "kms:TagResource", "kms:UntagResource", "kms:ScheduleKeyDeletion", "kms:CancelKeyDeletion", "kms:RotateKeyOnDemand" ], "Resource": "*" }, { "Sid": "Allow use of the key", "Effect": "Allow", "Principal": { "AWS": [ "${ADMIN_USER_ARN}", "arn:aws:iam::848625246342:root" ] }, "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*" }, { "Sid": "Allow attachment of persistent resources", "Effect": "Allow", "Principal": { "AWS": [ "${ADMIN_USER_ARN}", "arn:aws:iam::848625246342:root" ] }, "Action": [ "kms:CreateGrant", "kms:ListGrants", "kms:RevokeGrant" ], "Resource": "*", "Condition": { "Bool": { "kms:GrantIsForAWSResource": "true" } } } ]}Create the KMS Key.
Ensure AWS CLI is configured with the correct credentials:
aws configure
Run the following command to create the KMS key:
aws kms create-key \ --region us-east-1 \ --policy file://policy.json \ --description "Customer Managed Key for unravel use" \ --key-usage ENCRYPT_DECRYPT \ --origin AWS_KMS
This command will:
Create a Customer Managed Key (CMK).
Attach the provided policy to the key.
Create an Alias.
Replace ${KMS_KEY_ID} with the actual key ID:
aws kms create-alias \ --alias-name alias/unravelkmskey1 \ --target-key-id ${KMS_KEY_ID}eg: aws kms create-alias \ --alias-name alias/unravelkmskey1 \ --target-key-id c9f17070-2c94-4ef3-9b3a-fdf5865db8fcAfter key creation, share the AWS ARN with the Unravel team.
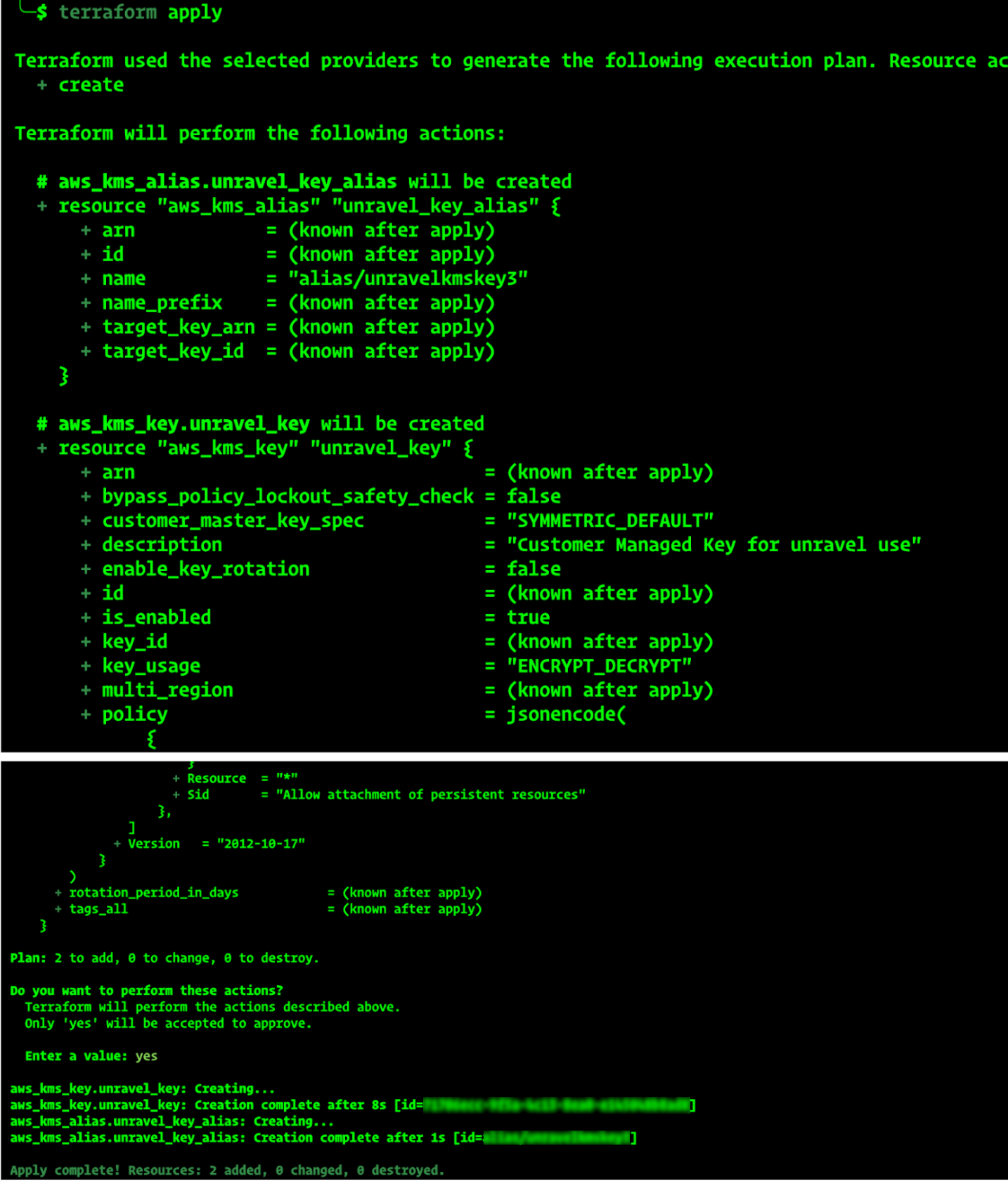
Using Terraform
To create an AWS KMS key using Terraform:
Once the key creation is complete, share the AWS ARN value with the Unravel team. You can find the ARN in the key description.
Create the Policy Document. Save the same policy JSON as policy.json.
{ "Id": "key-consolepolicy-3", "Version": "2012-10-17", "Statement": [ { "Sid": "Enable IAM User Permissions", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::${CURRENT_AWS_ACCOUNT_ID}:root" }, "Action": "kms:*", "Resource": "*" }, { "Sid": "Allow access for Key Administrators", "Effect": "Allow", "Principal": { "AWS": "${ADMIN_USER_ARN}" }, "Action": [ "kms:Create*", "kms:Describe*", "kms:Enable*", "kms:List*", "kms:Put*", "kms:Update*", "kms:Revoke*", "kms:Disable*", "kms:Get*", "kms:Delete*", "kms:TagResource", "kms:UntagResource", "kms:ScheduleKeyDeletion", "kms:CancelKeyDeletion", "kms:RotateKeyOnDemand" ], "Resource": "*" }, { "Sid": "Allow use of the key", "Effect": "Allow", "Principal": { "AWS": [ "${ADMIN_USER_ARN}", "arn:aws:iam::848625246342:root" ] }, "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*" }, { "Sid": "Allow attachment of persistent resources", "Effect": "Allow", "Principal": { "AWS": [ "${ADMIN_USER_ARN}", "arn:aws:iam::848625246342:root" ] }, "Action": [ "kms:CreateGrant", "kms:ListGrants", "kms:RevokeGrant" ], "Resource": "*", "Condition": { "Bool": { "kms:GrantIsForAWSResource": "true" } } } ]}Make sure to replace the placeholders:
CURRENT_AWS_ACCOUNT_ID: Your AWS account ID where the KMS key is being created.
ADMIN_USER_ARN: ARN of the IAM user or role that will manage the KMS key.
Create the Terraform configuration.
provider "aws" { region = "us-east-1"}# Create the KMS Key with the policyresource "aws_kms_key" "unravel_key" { description = "Customer Managed Key for unravel use" key_usage = "ENCRYPT_DECRYPT" # Referencing the policy from the external file policy = file("policy.json")}# Create an Alias for the Keyresource "aws_kms_alias" "unravel_key_alias" { name = "alias/unravelkmskey" target_key_id = aws_kms_key.unravel_key.key_id}aws_kms_key: This resource creates a Customer Managed Key (CMK) in AWS KMS, applying the policy defined in the policy.json file.
aws_kms_alias: This resource creates an alias (alias/unravelkmskey2) to make it easier to reference the KMS key.
Initialize Terraform.
terraform init
This initializes the Terraform working directory and downloads any required plugins.
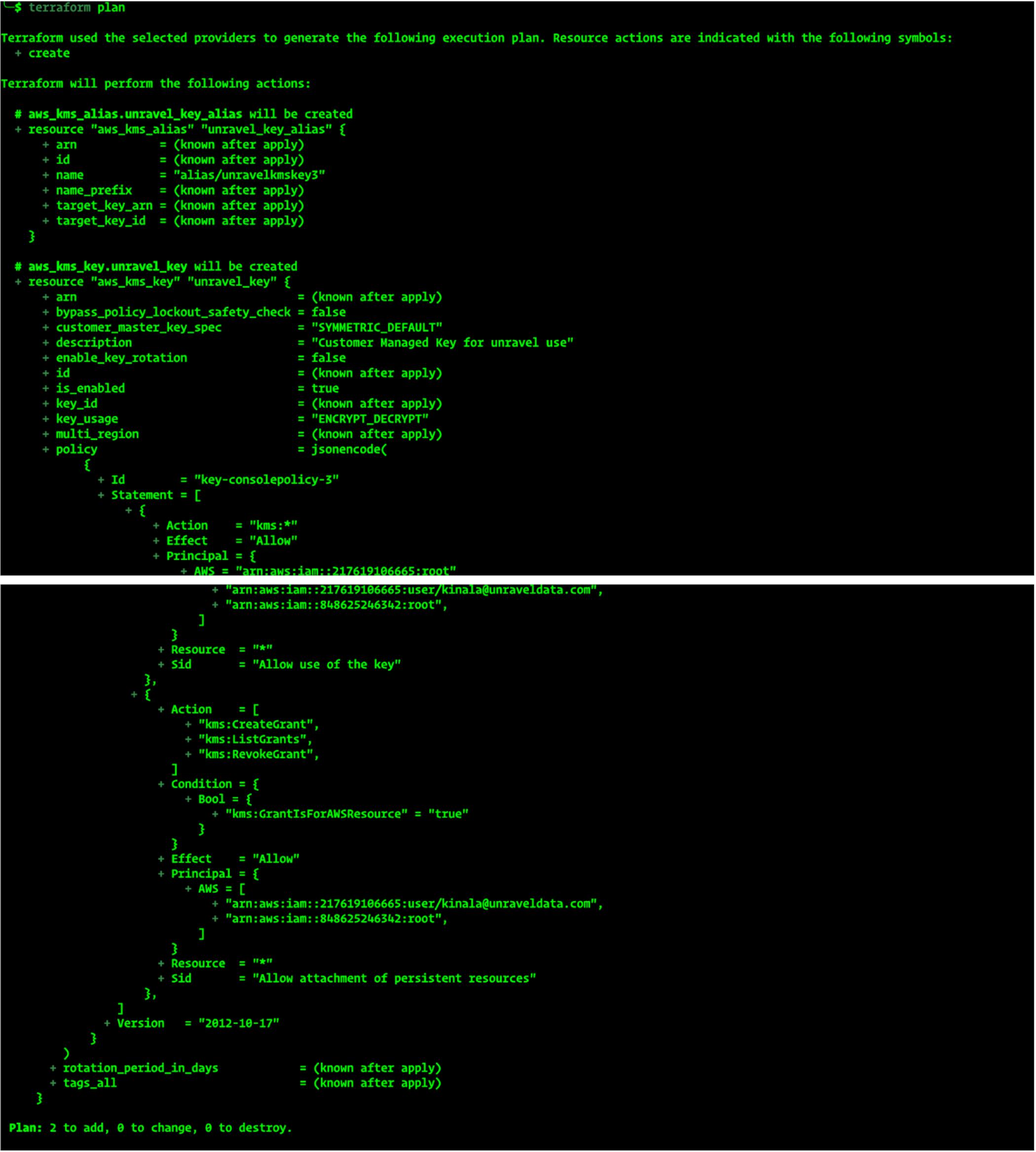
Plan the Changes.
terraform plan
This displays an execution plan outlining the resources Terraform will create or modify.
Apply Terraform.
terraform apply
When prompted, type Yes to confirm the action. Terraform will create the KMS key and alias name.