Enabling LDAP authentication for Unravel UI
You can configure lightweight directory access protocol (LDAP) by
Using UPN lookup and Group lookups using DN.
sAMAccount name to match users.
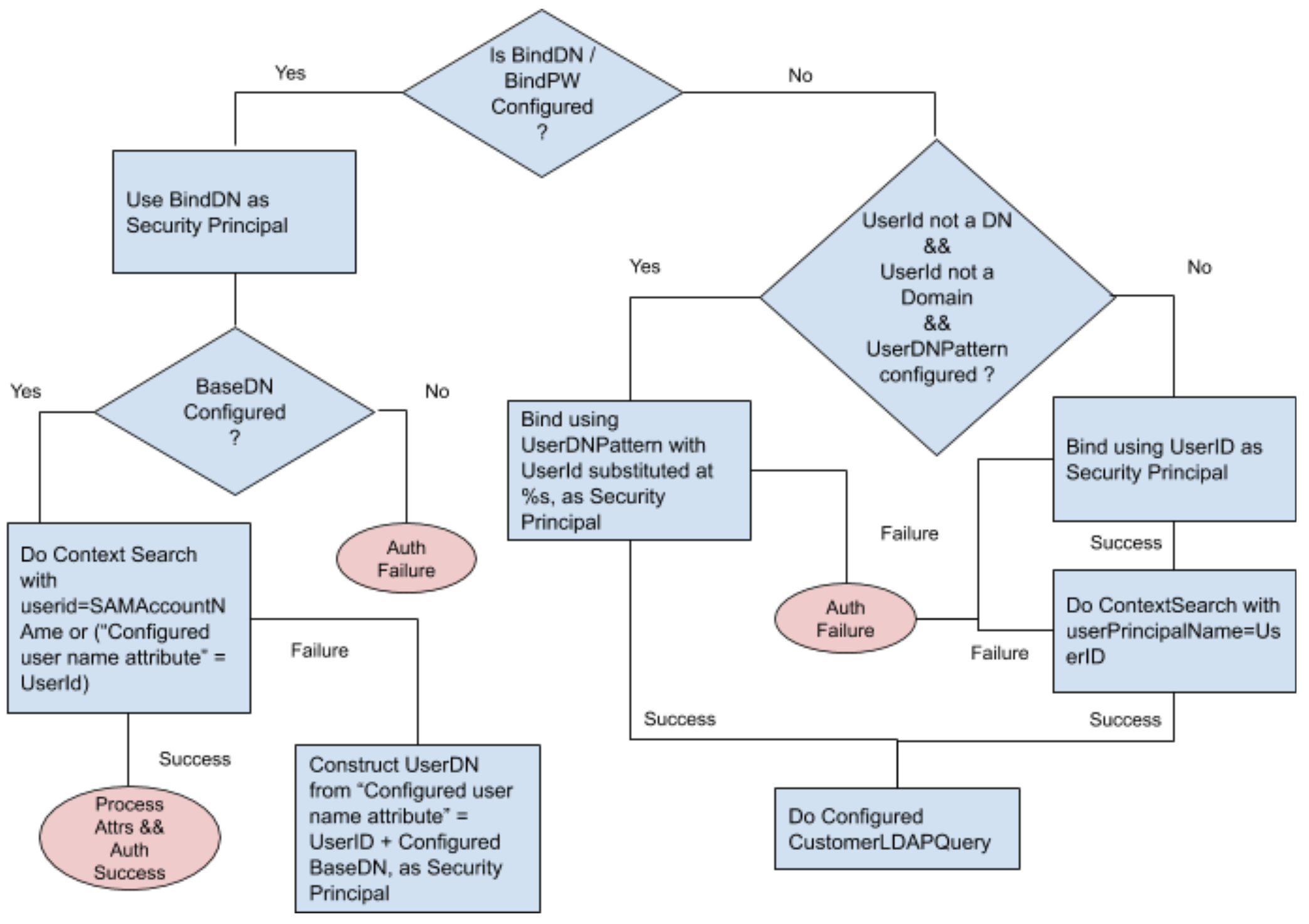 |
Important
You must restart the ngui module (/etc/init.d/ngui restart) after LDAP configuration.
Simple configuration using UPN lookup and Group lookups using DN
This configuration example is for the newer implementation of Unravel with MS Active Directory and for objects located in separate OUs. In this method the user lookup is on login id appended with the configured domain defined in /usr/local/unravel/etc/unravel.properties to make UPN (User Principal Name) for the lookup.
Note
This configuration doesn't
Work if objects in the directory don't have the expected UPN format.
Include bindDn and password which older implementations used.
Important
You must substitute your local values for the parameters and values used in the following examples.
Please contact your LDAP Admin if you don't know the following directory information.
Check that the object can be found and the user is part of the expected groups.
ldapsearch -v -h ariel.unraveldata.com -p 389 -D CN=sethbind,OU=seth,DC=unraveldata,DC=com -w unraveldata1! -b DC=unraveldata,DC=com -s sub "(userPrincipalName=commauser@unraveldata.com)"
Set the following properties in
/usr/local/unravel/etc/unravel.properties. Add these properties if they aren't found.#LDAP com.unraveldata.login.mode=ldap com.unraveldata.ldap.url=ldap://ariel.unraveldata.com com.unraveldata.ldap.baseDN=DC=unraveldata,DC=com com.unraveldata.ldap.use_jndi=true com.unraveldata.ldap.verbose=true #LDAP groups com.unraveldata.ldap.groupFilter=seth-test-group,seth-test-admingroup com.unraveldata.login.admins.ldap.groups=seth-test-admingroup
Advanced configuration where UPN can't be used.
This configuration uses sAMAccount name to match users. bindDN and password must be configured in /usr/local/unravel/etc/unravel.properties. It uses CN to match groups instead of DN which was used in the example above. The configuration uses bind user to get groups, then match it using CN to filter out groups located in com.unraveldata.ldap.groupFilter, as well as assigning admin users specified in com.unraveldata.login.admins.ldap.groups.
Important
You must substitute your local values for the parameters and values used in the following example.
Please contact your LDAP Admin if you don't know the following directory information.
Check that the object can be found and the user is part of the expected groups.
ldapsearch -v -h ariel.unraveldata.com -p 389 -D CN=sethbind,OU=seth,DC=unraveldata,DC=com -w unraveldata1! -b DC=unraveldata,DC=com -s sub "(sAMAccountname=commauser)"
Set the following properties in
/usr/local/unravel/etc/unravel.properties. Add these properties if they aren't found.#LDAP com.unraveldata.login.mode=ldap com.unraveldata.ldap.url=ldap://ariel.unraveldata.com com.unraveldata.ldap.baseDN=DC=unraveldata,DC=com com.unraveldata.ldap.use_jndi=true com.unraveldata.ldap.verbose=true com.unraveldata.ldap.bind_dn=CN=sethbind,OU=seth,DC=unraveldata,DC=com com.unraveldata.ldap.bind_pw=unraveldata1! com.unraveldata.ldap.guidKey=sAMAccountName #LDAP groups com.unraveldata.ldap.groupFilter=seth-test-group,seth-test-admingroup com.unraveldata.ldap.groupMembershipKey=member com.unraveldata.ldap.groupQueryFilter=(CN=seth*) com.unraveldata.login.admins.ldap.groups=seth-test-admingroup
What is the difference between the two group properties in LDAP configurations?
com.unraveldata.ldap.groupFilter: Lists the groups Unravel looks in for users who are allowed to log in.
com.unraveldata.login.admins.ldap.groups: Lists the groups Unravel looks in for users who are allowed log in as admins.
Important
com.unraveldata.login.admins.ldap.groups is a subset of com.unraveldata.ldap.groupFilter, i.e., a group defined in com.unraveldata.login.admins.ldap.groups must also be defined in com.unraveldata.ldap.groupFilter.
For example,
com.unraveldata.ldap.groupFilter=secs-lab-admins,secs-lab-users # the admins.ldap group is also defined in ldap.groupFilter com.unraveldata.login.admins.ldap.groups=secs-lab-admins
If a user is:
Not listed in the groups defined in com.unraveldata.ldap.groupFilter, they can't log in.
Listed in group defined in com.unraveldata.login.admins.ldap.groups, they are logged in as an admin.
Only listed in the groups defined in com.unraveldata.ldap.groupFilter, they are logged in as a non-admin user.